With more businesses than ever shifting their workforce to a remote setting, there are heightened security risks that remote work can introduce to your organization. In this article, we will outline some of the areas of vulnerability, and what you can do to mitigate these threats.
Whether you run a business remotely or are accommodating a remote work policy due to the coronavirus pandemic, the reality is that more and more businesses like yours are making this shift.
While your employees are likely grateful to be able to continue doing their job from the convenience of their own home, the unfortunate reality is that doing this comes with an increased risk to malicious security attacks. This could cause further unnecessary disruption to your bottom line than you’re already facing.
There were 3,813 data breaches reported from January through June in 2019 – a massive spike since 2017 - which exposed over 4.1 billion records.
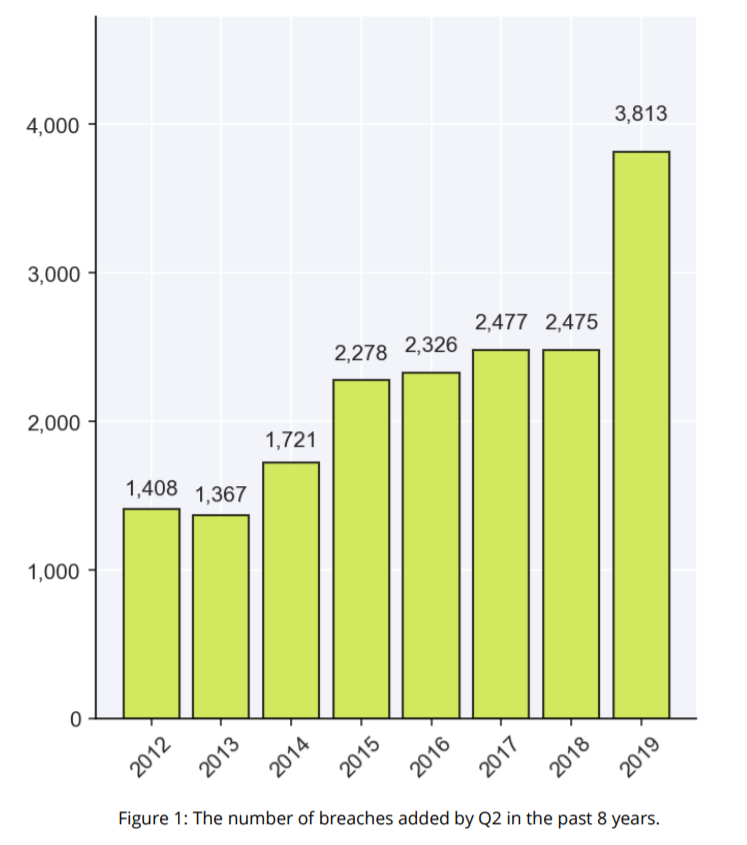
Image source: RiskBased Security
There is a lack of infrastructure in place to protect your business data from security risks when working remotely, as many employees switch to using personal devices or less secure networks to conduct their business activities:
For ecommerce businesses, or any business that involves collecting personal information like home addresses, phone numbers, and credit card information, the cost of dealing with a security breach that compromises this type of data could be enough to completely paralyze your organization.
The good news is, there are ways to combat these threats, and the first step is educating yourself on where some of the most vulnerable areas are when it comes to the security risks remote work can create.
Unlike your office, your IT department cannot control how network security is being managed when it comes to the homes of your employees. Chances are, their homes have little to no protocols in place to protect internet security, such as WEP instead of WPA-2.
You’ve likely come across what seems like an honest, legitimate email, only to look a little closer and realize the link, or the email address of the sender, is suspicious. When an employee clicks on one of these links or downloads an attachment, hackers can gain direct access to their device.
Note: COVID-19-themed phishing attacks are on the rise, often tricking people into downloading statistics and other information about the pandemic, as seen in the example below.
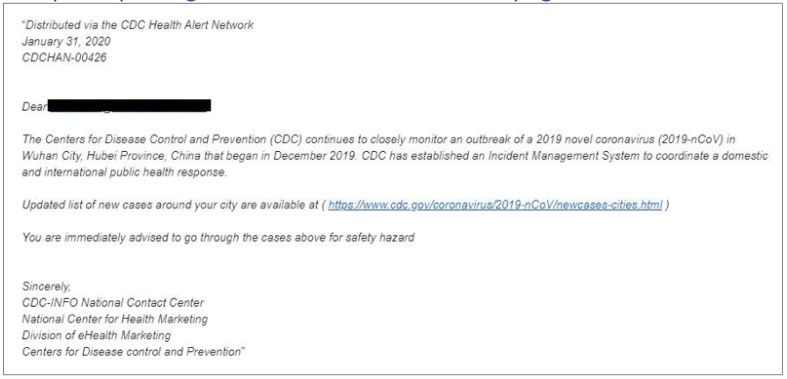
Image source: Norton
If your remote working employees are using their personal computers at home instead of their office ones, they likely have a simpler password – if they have any password at all – to log onto their system. Simple passwords are much easier for hackers to attack. In addition to this, if your employee uses that password for other tools and systems as well, they could be exposing themselves and potentially your business to even more security risks.
System updates and other important patches often come with security updates to deal with some of the above threats. However, a surprisingly large number of people do not update their computers often enough, putting them at a higher risk of falling victim to an attack.
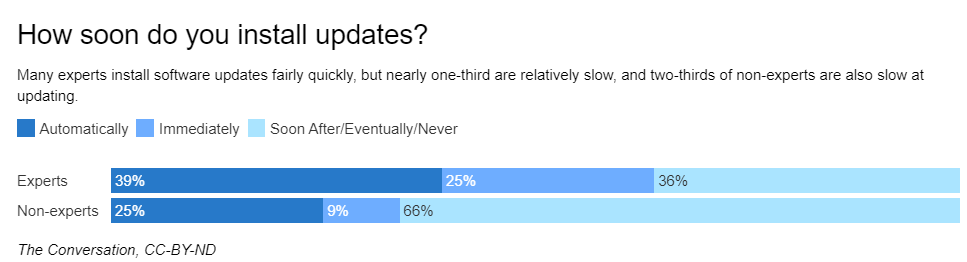
Image source: Google Research
Now that you have more knowledge on where some of these larger areas of concern are with your remote workforce, it’s time to focus on some techniques you can deploy to help mitigate attacks like these from happening in the first place.
If you have the ability to replace hardware-based legacy VPNs in exchange for a more robust, cloud-based equivalent, it will matter less what device your employees are working from. Legacy VPNs are challenging to deploy efficiently, and don’t have the same flexibility when it comes to managing security risks remote work may invite.
While these are two separate tactics, using one or even both will help fortify your remote defenses:
Consider limiting access your staff has to certain files, folders, and portals. If their job does not require them to have access to your entire company database, start implementing permissions so that you’re mitigating the chances that vital documentation is compromised in the event of a security lapse.
Another thing you can do is set expiration dates on certain types of documentation as well, so that after a certain period of time it expires and can no longer be viewed. This can be helpful particularly when managing personal user information.
Knowledge is power when it comes to mitigating security risks that working remotely creates for your business. Take the time and provide opportunities to educate and walk your staff through your organization’s security protocols. Here are a few good areas to cover:
Enacting countermeasures like the ones we’ve covered above isn’t an easy thing to do, and many of the tactics require time and patience to set up properly. Despite the effort however, time spent fortifying your business today will be less time spent doing damage control tomorrow.
By following some of the above tactics mentioned, you will be adding additional layers of security to your business and mitigating the risk of dealing with yet another unwanted complexity during the coronavirus pandemic.